Ics Cyber Security Engineer Salary

Arc Cybersecurity Model Shows Passive Vs Active Defense Cyber Security Technology Today Network Engineer

Cis Controls Used Across Industries Government Healthcare Engineering Education Cyber Security

Cia Triad Security Priorities Security Cyber Security Priorities

Cybersecurity Maturity Model Cyber Security Device Management Solutions

How Secure Are Your Process Safety Systems Chemical Processing

Ics Robert M Lee

Nccic Branches Cyber Security Process Control Communications

Pin On Mgs News Information Intelligence
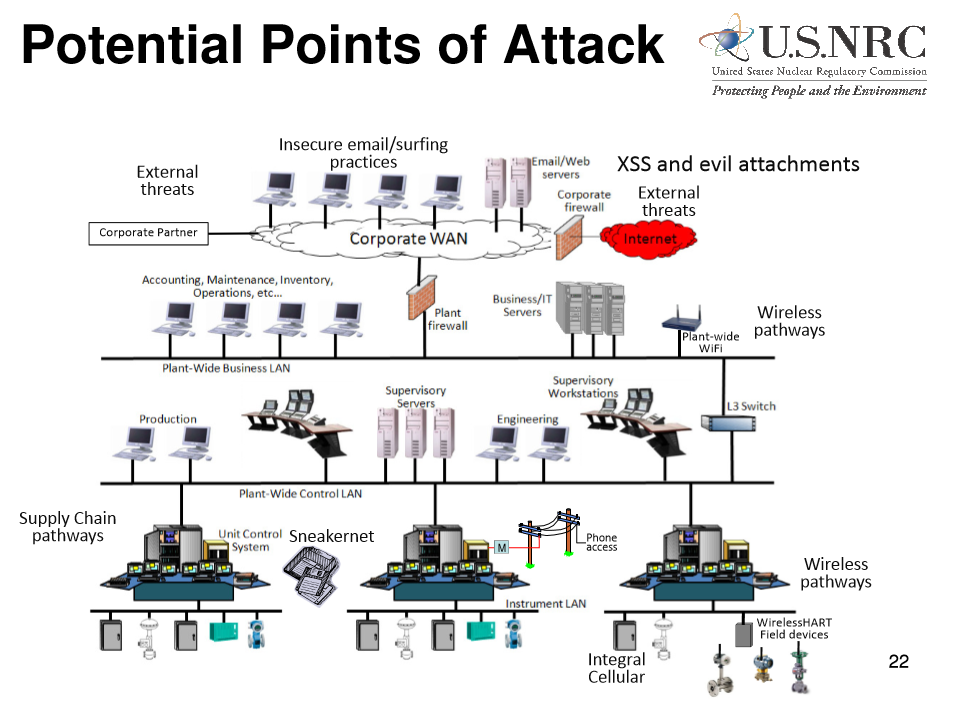
Is Your Manufacturing Facility Vulnerable To Cyber Attacks Formaspace

How Stix Taxii And Cybox Can Help With Standardizing Threat Information Taxii Stix Cybox Diagram Cyber Security Systems Engineering Homeland Security

Vmtabf07kydj0m

Prodefence Cyber Security Services Malware Pentesting Siemens Logo Siemens Electronics Logo

Collaboration Delivers Unified It And Ot

Cyber Integrity Pas In The News

Eu Cybersecurity Dashboard Summary Bsa The Software Alliance Cyber Security Alliance Dashboard

What Are A Few Top Cyber Security Companies In India Quora Security Solutions Cyber Security Security Companies

Industrial Cybersecurity In 2019 Risks And Recommenations

Pin On Cyber Security Consultant Usa

Home How To Find Out Cyber Security Malware

Better Data Security Through Classification A Game Plan For Smart Cybersecurity Investments Data Security Cyber Security How To Plan

Ics Cyber Kill Chain Cyber Security Optimization Development

Subcategories 1 1 Cybersecurity Framework Risk Management Strategies Risk Management

Industry Articles Yaskawa

Applied Risk Ics Singapore 2019 Hacking Building Management Systems Emerging Cyber Security Legislation Advanced Ics Hacking Training Applied Risk

Https Encrypted Tbn0 Gstatic Com Images Q Tbn 3aand9gcqpqlee0ltovt6t5pidgnnhpmkpthxzdeft57q4m51tmekwr1h Usqp Cau

Functional Safety And Security Ics Cyber Security Is Part Of Functio

What 39 S In The Nist Cybersecurity Controls Catalogue Update Cyberscoop Cyber Security Catalog Control

Imagine H2o Announces 2018 Accelerator Imagine Cyber Security How To Apply

How Stix Taxii And Cybox Can Help With Standardizing Threat Information Visualizing Stix Threat Event Management System Organization Help

How To Build A Growth Team Lessons From Uber Hubspot And Others 50 Slides At Andrewchen Hubspot Lesson Growth